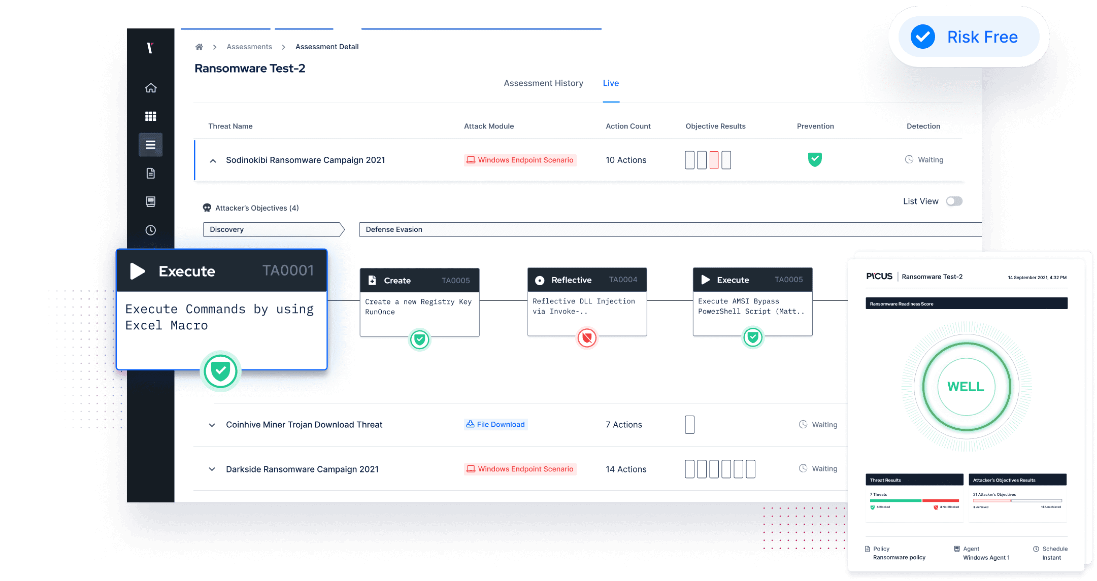
Leverage Picus’ award-winning Security Control Validation solution to simulate real-world vulnerability exploitation attacks in minutes and gain a holistic view of your controls’ effectiveness against their cyber attacks at all times. Identify threat prevention and detection gaps AND empower your team with actionable mitigation recommendations for quick remediation and compliance maintenance.